Developing Secure Wireless Audio Links
投稿人:电子产品
2015-10-08
While we may not care (beyond a bit of annoyance) if anyone taps into our music stream, we do care if someone is listening to our conversations, voicemails, or eavesdropping by turning on the microphones built into our smartphones, laptops, computers, tablets, or even our TV. Also, we should care since audio links can also serve as modem-style digital links; beyond simple eavesdropping, control of our devices could be at risk.
What’s more, there are trusting systems in place like intercoms, baby monitors, toy robots, and drones that use simple and low-cost narrow-band AM or FM links to transmit fairly good audio quality signals. Here, too, the problem, especially with a wireless link, is that anyone can tune in and listen if they really want to.
This article looks at wireless-audio security techniques and discusses development kits and the safeguards available to help assure privacy and security. This includes standard encryption and decryption techniques as well as audio jammers and scramblers that make conversations and music garbled and indistinguishable. All parts, data sheets, tutorials, and development kits referenced here can be found on DigiKey’s website.
Made to distort
Content providers use protection schemes to safeguard against piracy. One example is called Secure Audio Path1 (SAP) and is a technique used by operating systems and ISPs to decrypt and decompress audio and then wrap a layer of cryptographic noise around the audio content. SAP also can provide a means for maintaining copy protection for music by ensuring that it is not intercepted by an unauthorized application before it reaches the sound card on a consumer’s computer (Figure 1). This technique allows a low-quality sample of the audio stream to traverse through the cloud and networks to find its way onto your player device.
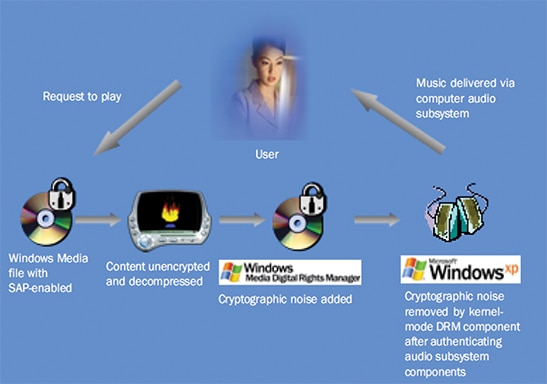
Figure 1: The audio industry has a vested interest in maintaining a secure music delivery path. Although a popular technique to do so is called Secure Audio Path, the audio is not scrambled and it is not really secure.
While some are happy with lower-quality audio as long it is free, others are motivated to legally purchase the audio tracks and will then get a pristine version of the audio after authentication. While this is called secure audio, it is not since the audio is not scrambled and indiscernible.
To truly guard against piracy and protect privacy, the actual audio must sound like noise to the un-authenticated node. To do this, audio can be scrambled in the analog domain, the digital domain, or both. One established technique in the analog domain is voice inversion that mixes frequency components with other signals from the carrier wave. The amplitude-modulated speech is then sideband filtered to make the resulting signal noisy and very hard to distinguish.
Note that carrier frequencies must also be in the audio range since transceiver links for audio are optimized for this frequency range. Note also that this technique is easily defeated by hardware and/or software techniques that can recover a good quality signal despite the scrambling. However, like an alarm sticker on a window, it may deter 90 percent of the incidental and random eavesdroppers who do not want to waste time figuring out how to de-scramble.
Digital scrambling
The term scrambling as it initially applies to digital circuits is a class of circuits that converts input data streams into apparently random output streams. Seeded pseudo- random feedback techniques are used to invert key bits algorithmically and can assure long strings of 0’s or 1’s will not occur (Figure 2).
While the initial intent of digital scramblers was to enable accurate timing recovery on receivers for synchronization, and to disperse the power spectrum to help meet spectral-density power constraints, it is also a useful technique to distort an audio stream and make it harder to recover.

Figure 2: A pseudo-random multiplicative scrambler (Top) and de-scrambler (Bottom) can easily be implemented in logic or software once the data is in digital form.
Encryption and decryption standards can also be used to mask audio content, and this seems to be the most widely used security scheme, but it also has issues. First, a processor of suitable class is needed to simultaneously monitor and control A/D and D/A stages, possibly do digital software-based filtering, memory, and buffer management, and perform encryption algorithms in real-time so as not to drastically affect latency and digital delay.
Second, a seeded key exchange must take place in some manner, and wireless snoopers can pick up any packet being sent if it is in close enough proximity. Third, data logging of signals can allow off-line processing to break a key and recover the audio stream at a later time. Once quantum cubit processor elements become more available to the mass market, all key-based encryption schemes could become null and void.
Secure audio links: parts and dev kits
Development systems and eval kits are the best way to learn, test, experiment, develop, and refine a new design. Especially when securing audio links. While standards abound, proprietary encryption is not a bad thing. It makes it that much harder for a would-be intruder to learn your secret sauce.
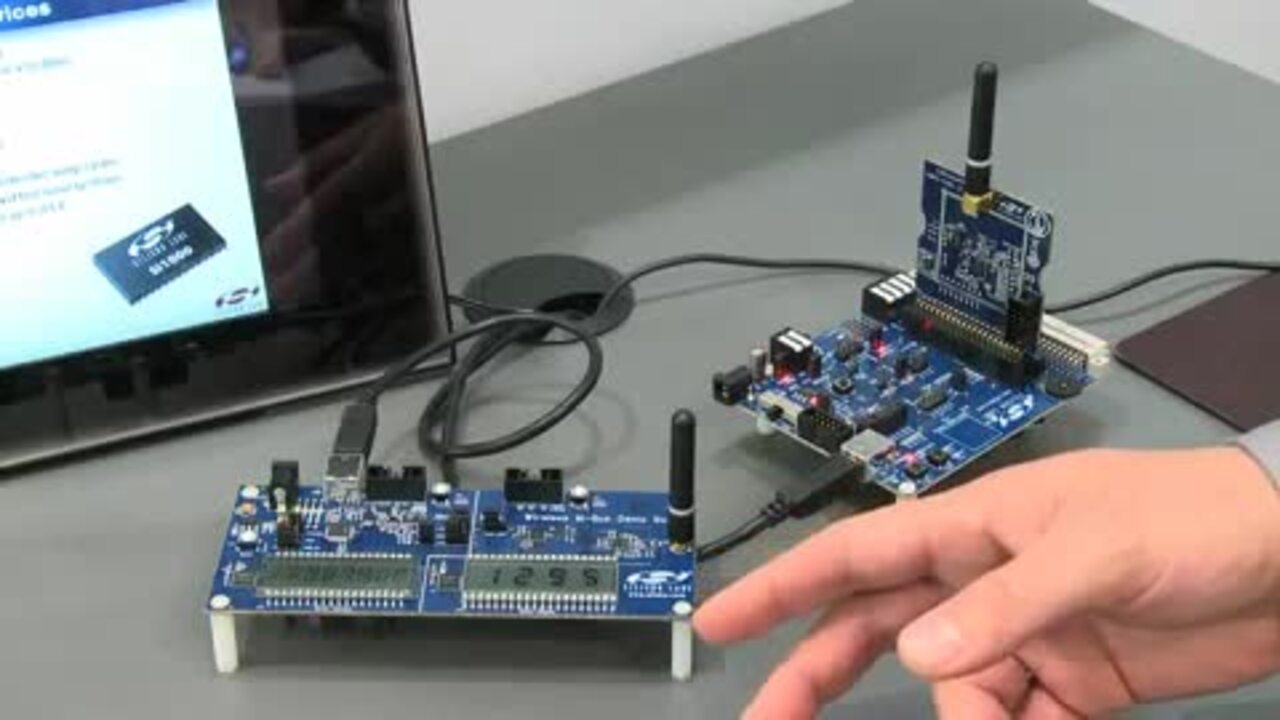
Modern devices mostly use Bluetooth for audio and several mixed-signal development kits support Bluetooth audio designs. Take for example the Sparkfun WRL-12849 Modular Audio RN52 Breakout Module for Bluetooth audio (Figure 3).
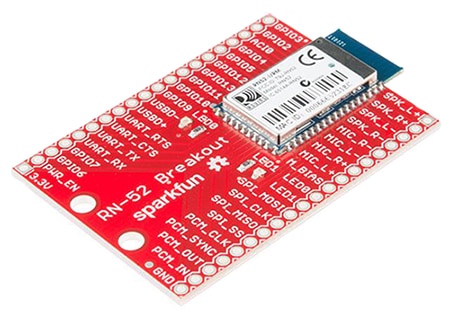
Figure 3: Wireless chips and modules often are supported in breakout form like this OEM or development wireless board with audio support.
The RN52 is a postage stamp-sized, command-driven fully qualified and SIG-certified Bluetooth 3.0 (legacy) module with embedded antenna, GPIO pins, and two differential audio channels for stereo streaming of high quality audio. While configurable over a UART using a command/response scheme, it also has IIC and S/PDIF interfaces for external CODEC support.
Analog scrambling can be tested directly, but code will need to be developed to run in the internal 16-bit RISC processor if you want to manipulate the on-chip audio DSP blocks (Figure 4).

Figure 4: Bluetooth devices with native DSP functionality may be used if designers have access to the internal code. This can sometimes be obtained under NDA.
Wi-Fi connectivity offers the possibility of a higher bandwidth data link, which will either permit higher quality audio or more channels. It also offers the benefit of a dynamically routed and switched network that can use different routing paths for mobile applications.
As an example of a useful wireless audio-link development tool, consider the Texas Instruments CC85XXDK, a member of the company’s PurePath wireless family. Single-, dual-, and quad-channel devices support high-quality digital audio links for wireless streaming (5 Mbit/sec rate) with sample rates up to 48 KHz/channel of 24-bit width. Parts like the TI CC8520RHAT use adaptive frequency-hopping spread spectrum with forward-error correction. In addition, buffered retransmitting allows error-free mode which is not critical in audio, but is with control systems.
Several other wireless microcontroller development kits are ready to use with support for custom-code development as well as interfaces to standard audio streams that have been scrambled or encrypted. The dev kits with direct audio support may be a good place to start.
The bottom line is that there is a need for secure, modern-day audio links despite the fact that many use spread-spectrum frequency hopping. Since many of the wireless audio-link kits currently available don’t directly support advanced DSP functions in a native way, expect to see more solutions emerge.
For more information on the parts discussed in this article, use the links provided to access product pages on the DigiKey website.
References
免责声明:各个作者和/或论坛参与者在本网站发表的观点、看法和意见不代表 DigiKey 的观点、看法和意见,也不代表 DigiKey 官方政策。