Secure Remote Updates Extend Embedded System Capabilities and Lifetime
投稿人:电子产品
2015-09-30
Embedded systems are at the heart of many industrial applications that demand long product lifetimes while being responsive to feature updates and bug fixes. Security concerns, in particular, can drive requirements for frequent code updates to stay ahead of hackers and malicious intruders. Including a remote-update facility—if it can be secured—can dramatically extend the useful lifetime of just about any embedded system.
This article will explore the wide variety of remote-system updates used in contemporary embedded systems by showing several different requirements and approaches. Future requirements for even more responsive embedded systems will also be discussed as will recent innovations in MCU capabilities that can determine the direction of future enhancements.
Secure embedded system updates
Embedded systems are often connected to a network to transfer information from “edge” devices to central controllers. Central controllers are, in turn, connected to storage units, gateways, and traffic aggregation units all using a network connection. In order to simplify the installation of code updates and bug fixes the interconnect network is also used to download updates to programmable devices. These updates can simply be new parameters to adapt to environmental changes or they can be complete code “replacements” providing new features and capabilities.
Updates need to be done in a secure manner or attackers could hijack the update process, replacing reliable code with their own programs. Often these attacks leave start-up code that executes prior to future updates so that the inserted code can persist even after an attempt to update the “infected” system. Several approaches are used to protect remote updates and they vary in complexity depending on the value of the system as a target to a hacker. Clearly, systems that handle financial data are obviously in need of protection, but even a system you might not think of as being vulnerable may require increased security. Often it’s the element on the periphery of a more complex system that provides attackers with an easy in-road. For example, an intelligent thermostat or building control system might allow attackers an easy way into a data aggregation sub-system and then into the central controller of a financial institution.
Security methods for remote updates
One of the most frequently used methods for securing data within an embedded system is to use encryption and decryption to protect sensitive data. Standard cryptographic functions along with secure keywords are typically used in security algorithms and embedded systems need to provide these capabilities in order to send and receive secure data. Security algorithms such as AES (Advanced Encryption Standard) and DES (Data Encryption Standard) are some of the most common functions you should look for to support secure communications.
More and more frequently edge nodes are using wireless communications to minimize installation costs and to allow more flexibility in deployment. These devices can also use a secure remote update capability and may even want to transfer regular data securely, too. Devices with embedded hardware that support common cryptographic standards and wireless connectivity will be a good fit for these applications.
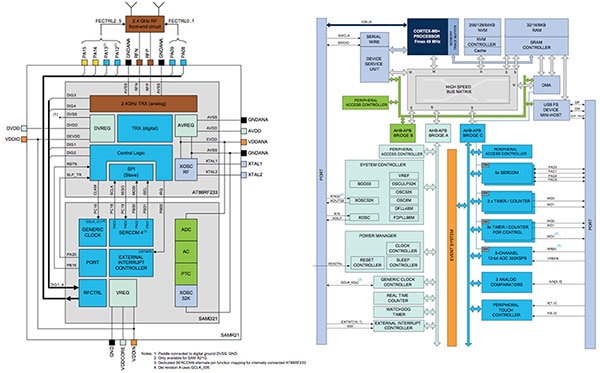
One example of an MCU-based device with these characteristics is the Atmel SMART SAM R21 wireless MCU. The block diagram of the device is shown in Figure 1. The left side of the figure is the full device with the wireless section shown at the top and the MCU section shown at the bottom. On the right side of the diagram is a more detailed view of the MCU section showing the processor and all the peripheral blocks. The two sections (actually separate devices) are connected using an SPI port making communications very simple to program.
Figure 1: Atmel SAMR21 wireless MCU block diagram. (Courtesy of Atmel)
The MCU can be used to manage wireless communications and with security algorithms built into the wireless device (AES is supported for all data communications) secure remote updates and secure data communications can be seamlessly implemented. In some systems multiple “boot” images might be maintained using off-chip memory. In these cases the external image would be encrypted as well so that it could not be easily copied (or even replaced) by hackers with hardware access to the system.
Ethernet connectivity: the main backbone
Wireless connectivity is a good fit for edge-node devices but once data is aggregated Ethernet is often used to implement a backbone network to carry higher bandwidth traffic. MCUs that implement multiple Ethernet connections with a focus on Industrial Ethernet, supporting IEEE1588, are most useful for these types of systems. Often significant off-chip memory, a variety of serial interfaces, and advanced human-machine interfaces (HMI) can be required when these systems need to be controlled or monitored locally.
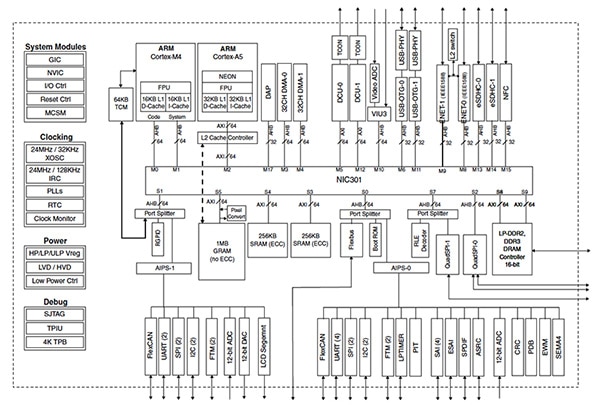
Several modern MCU families support these key features and the Freescale VF6xx MCU Family serves a good illustrative example (Figure 2). These devices have dual CPUs based on the ARM Cortex-M4 and Cortex-A5 architectures. These processors deliver significant processing capabilities appropriate for managing high-bandwidth communications, data aggregation, data storage, and HMI control for the most advanced application requirements. The ARM processors support the standard ARM TrustZone security functions making it easy to protect and authorize confidential data and processes.
Figure 2: Freescale VF6xx MCU block diagram. (Courtesy of Freescale)
In the most security-conscious applications the dual processors available on the VF6xx can be used to separate security-related functions from those that are not security related. By using trusted memory locations and cryptographically strong security processes with only the designated processor it becomes much more difficult for a remote attack to be successful. The VF6xx also has advanced tamper-detection capabilities that can be used to shut down attempts to access the hardware in an unauthorized manner. Implementing multiple layers of security is one of the best approaches to protecting an embedded system from even the most aggressive attacks. Look for devices with multiple layers of security when you need a robust implementation.
Other important functions
When selecting an MCU for embedded applications it’s still important to consider the additional functions you will need to support for your target application — not just the remote update-related ones. In fact, many modern MCUs now support fairly robust remote functions and you can often start your search assuming medium- to high-end MCUs will have baseline remote-update functions included.
As an example, let’s consider a health-and-wellness application that requires significant analog-interface capability. The STMicroelectronics STM32F3x family of MCUs supports several analog functions including a 16-channel 12-bit ADC, a 9-differential channel sigma-delta converter-based ADC, a 3-channel 12-bit DAC, and two general-purpose comparators. These resources are just right for a variety of medical and wellness applications where analog sensors are required to make measurements of heart rate, blood oxygenation, and respiration (to name just a few examples).
The STM32F3x has a useful boot-configuration mode-selection capability, shown in Figure 3 below, which can use either Flash memory, System memory, or embedded SRAM as the boot location. This facility works with an embedded-configuration bootloader stored on-chip (programmed by ST during production) to ease remote updates.
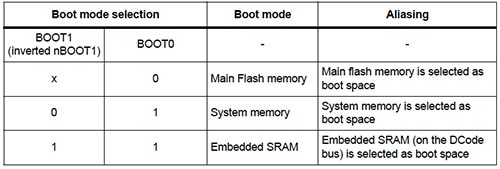
Figure 3: STMicroelectronics STM32F373 boot options. (Courtesy of STMicroelectronics)
As remote updates have become more popular, many MCUs support a bootloader function that takes an off-chip image (often provided over a serial interface) and then programs the image into Flash memory. The STM32F3x can use either a USART port or the USB port as a data source. This significantly simplifies the remote-update process and eliminates the need to write this type of code yourself. Additional layers of security can be implemented (either internally to the STM32F or by using an external secure-memory device) depending on the requirements of the target application.
Not every MCU has hardware-based security
When looking at low-end MCUs it’s not common for advanced hardware encryption functions to be supported. This does not mean we cannot use these devices when remote-update capabilities are important. Often low-end MCUs are used in conjunction with other devices, perhaps as intelligent peripherals controlling or monitoring environmental aspects of a larger system. In these cases there is probably a higher-end device that communicates and controls the low-end MCUs. The higher-end device can provide the security-related capability and can be leveraged over several other devices. This can be much more cost effective and can simplify the implementation and management of remote updates.
As an example, let’s look at an application that needs a very-low-power intelligent peripheral that measures air flow, temperature, and voltages in a communications rack. An MCU like the Renesas RL78/G14, shown in Figure 4 below, has the resources required to make periodic measurements, collect and store logged data, and communicate to the central controller when measurements go out of bounds. A serial interface can be used by the controller to update configuration information perhaps for simple bug fix “patches” or even for a full update of the on-chip program.
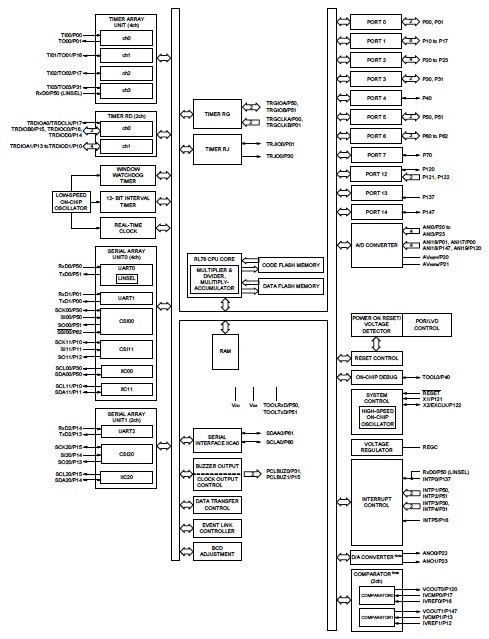
Figure 4: Renesas RL78 MCU block diagram. (Courtesy of Renesas)
On the RL78/G14 the on-chip data flash can be used to store logged data as well as code updates, patches, or changes to configuration information. Data flash is typically easier to write to making it an efficient place to store update information either permanently or as a stage prior to updating code memory, which takes longer and is more involved. Look for opportunities to use data flash to simplify remote updates either as a staging area or as a patch location for simple bug fixes.
Conclusion
Remote updates, whether simple or complex, can extend the lifetime of embedded systems significantly. Do not overlook the need to implement a variety of layered security features to protect the remote update from interference by malicious entities. Modern MCUs are adding new features to help simplify the addition of remote updates to embedded systems so make sure you are aware of the features available on your target MCU.
For more information on the parts discussed in this article, use the links provided to access product pages on the DigiKey website.
免责声明:各个作者和/或论坛参与者在本网站发表的观点、看法和意见不代表 DigiKey 的观点、看法和意见,也不代表 DigiKey 官方政策。








 中国
中国