Using Biometric Sensing to Verify Identity
投稿人:电子产品
2015-09-17
Much effort has been made and a great deal has been accomplished in the creation of biometric sensing technology that identifies, with little doubt, just who we are. Available methods of identification include fingerprint analysis, facial recognition, unique iris pattern identifiers, and more. There is a comprehensive portfolio of biometric ID technologies available to engineers, with others still on the drawing board, that provide varying degrees of authentication and carry an equally large variety of price tags.
The good news is that biometrics is sufficiently advanced to be almost unnoticed in day-to-day living. Many of our smartphones and tablets now employ some form of biometric identification — usually fingerprint analysis — to provide access and protect our credit cards, bank accounts, and personal data.
Biometrics is fast replacing outdated employee identification systems that use traditional access cards. These cards present serious vulnerabilities, particularly when they are lost or stolen. To compensate, business offices, airports, and government agencies either implement redundant, resource-intensive measures for worker access control, or they leave critical areas vulnerable to fraud and illegal entry. By adding a biometric security layer to the existing security platform, fraud can be eliminated and security significantly improved.
Following the events of 9/11 the Department of Homeland Security has spent well over $100 million on biometrics, and in the last eight years the Defense Department alone has spent an estimated $3.5 billion on the technology; in trying to separate insurgents from the general public, for example, the U.S. military collected fingerprints, iris scans, and facial images from millions of Iraqis and Afghanis.
Today’s biometric solutions are designed to perform even in the most difficult circumstances. Facebook, for example, has developed an advanced facial recognition software program that recognizes an individual even when their face is not visible. Once an individual is tagged and entered into the Facebook system, the technology is said to be able to recognize people based on body type, hair, pose, posture, and clothing, for example.
Similarly, a MasterCard version uses a selfie as the basis of security. Users take the selfie to authorize a purchase at the time the purchase is made to confirm their identity and that they indeed are the buyer. Users must blink when taking the photo to prevent hackers from taking a picture of a previously taken photo. The application also allows for users to scan their fingerprints, confirming a second form of ID via Apple Pay.
Technology options
That the underlying sensor technologies have made great progress is evidenced by Omron’s Human Vision Components (HVC) module (Figure 1). It is based on the use of 10 algorithms or functions that include face detection, face recognition, gender, age, expression, facial pose, gaze and blink estimations, and hand and body detection. A person in various facial poses, expression, and illumination conditions can be recognized by his or her face via comparison with faces already registered in the database. The sensor can also estimate the age and gender of a face in various expressions and illumination conditions. The HVC sensor will even automatically estimate various facial expressions (neutral, happy, sad, angry, and surprised).
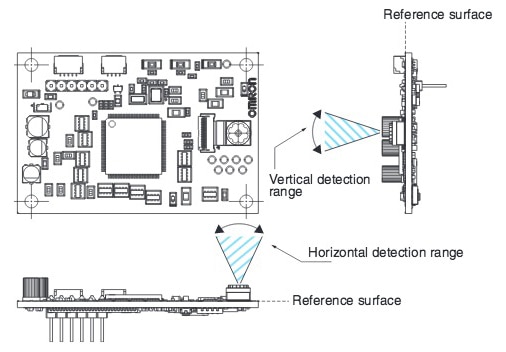
Figure 1: Image input specifications for horizontal and vertical detection ranges with the Omron B5T-01001 (G) module.
Omron integrates its OKAO Vision image-sensing technology, a camera, processor, and an external interface onto a single 60 mm x 40 mm PCB. The HVC acts as a sensor and uses a UART interface to provide data about the person(s) it sees. In addition to security applications, capturing such data can be beneficial whenever people interact with machines, from consumer to industrial environments.
To assist engineers, Omron also provides a Human Vision Components Demo Kit designated B5TE001SG.
The technology behind authentication usually involves pattern recognition. A good example of the state of this art can be found in the CM1K Pattern Recognition Chip by Cognimem Technologies (Figure 2). This first ASIC version of the CogniMem neural network features 1024 neurons working in parallel that are capable of learning and recognizing patterns of up to 256-bytes in just a few microseconds. A neuron is an associative memory which can autonomously compare an incoming pattern with its reference pattern.

Figure 2: Functional diagram of the CogniMem CM1K.
Two non-linear classifiers supported by the chip classify patterns even with ill-defined data, unknown events, and when context and working conditions change. Based on low pin-count and low power, it is used as a companion chip for smart sensors and cameras.
Features include the ability to recognize one vector among 1024, or any number, in 10 μsec with a 27 MHz clock. This recognition time is independent from the number of models. The chip learns a vector in only 10 μsec. It saves and loads models (i.e. the knowledge base), and uses simple RTL instructions with less than a dozen registers. It offers parallel and serial communications and an optional digital input bus directly interfaced to a recognition stage.
The pattern recognition technology is, according to the company, based on a simple architecture. It is a chain of identical neurons operating in parallel. During the recognition of an input vector, the neurons communicate briefly for 15 clock cycles to find the best match. The CM1K also integrates a built-in recognition engine that receives vector data directly through a digital input bus and broadcasts it to the neurons, returning the best fit category 3 μsec later. It can also optionally extract a 1-D vector from 2-D video data.
Applications include the ability to assist identification across image and signal recognition as well as data mining. Applications in the image-recognition area include face recognition, gaze tracking, target tracking and identification, and object recognition. In the signal-recognition segment, it is used for speech recognition and voice identification, and in data mining its uses include bio-informatics and fingerprint identification.
It is not only the ability to accurately authenticate an ID that’s critical to biometric applications. Once user information is in place, it is essential that the data remain safe. To that end, there is the MikroBUS Fingerprint click Development Board (Figure 3), a click-board solution for adding biometric security to designs. Featuring the GTS-511E2 module, which is claimed to be the thinnest fingerprint sensor available, the module has a CMOS image sensor complete with a special lens and covering to record real fingerprints and resists 2-D fakes. It also has an STM32 MCU for image processing.
Fingerprint click can communicate with the target board MCU through UART (TX, RX) or SPI (CS, SCK, MISO, MOSI) lines. It also carries a mini USB connector for connecting the click board to a PC — which the supplier says will generally be a more suitable platform for developing fingerprint recognition software, due to the processing power required for comparing and matching inputs to a large database of existing images. The board is also lined with additional GPIO pins giving more access to the onboard STM32. Fingerprint click is designed to use a 3.3 V power supply.

Figure 3: The MikroBUS Fingerprint Development System adds security to biometric apps.
Underlying algorithms
The importance of algorithm development in biometrics-based applications cannot be overstated. Generally speaking it is divided into two groups, geometric and photometric. The first concentrates on distinguishing features and the latter is a statistical approach that translates an image into values and uses the values to compare them with templates that assist in eliminating variances.
A more recent trend is 3-D face recognition that employs 3-D sensors to gather information on a face’s shape and uses it to identify such distinct features as eye socket contour, chin and nose shape, and more. The benefits of this method are that it is not subject to distortion with lighting changes and it is able to identify correctly using a variety of angles of the face, rather than a straight-ahead shot. The 3-D data points used yield improved recognition accuracy.
When one considers the rapidly improving underlying sensors, new and highly integrated chips and advanced algorithms, it is easy to see why biometric security and identification is exploding. Indeed, a marketsandmarkets report issued in May predicts that the market for biometric systems is expected to reach $24.4 billion by 2020, representing a CAGR of 17.9 percent between 2015 and 2020.
For more information about the parts discussed in this article, use the links provided to access product pages on the DigiKey website.
免责声明:各个作者和/或论坛参与者在本网站发表的观点、看法和意见不代表 DigiKey 的观点、看法和意见,也不代表 DigiKey 官方政策。







