Employing Tamper Detection and Protection in Smart Meters
投稿人:电子产品
2015-06-17
Smart meters can enable great flexibility in optimizing energy usage but also can present additional opportunities for theft of electricity through tampering. Besides their vulnerability to older forms of physical tampering, these devices face more sophisticated forms of attack by hackers. For engineers, tamper-proof smart-meter design can build on a broad range of design methods and sophisticated devices from manufacturers including Analog Devices, Atmel, Freescale Semiconductor, Maxim Integrated, NXP Semiconductors, Pulse Electronics, STMicroelectronics, and Texas Instruments, among others.
According to industry analysts, annual electricity theft amounts to nearly $90 billion worldwide with well over half of that occurring in the world’s emerging markets including India, Brazil, and Russia. At the same time, electricity theft is as old as the utility meter itself and draws on a variety of methods that alter the meter and its inputs in an attempt to influence the meter’s energy measurements.
For example, traditional analog utility meters were notoriously susceptible to relatively simple physical attacks (Figure 1). Typically, energy thieves would break into the meter to affect the measurement mechanism itself or use magnets to confuse the current sensing mechanism – typically resulting in a falsified reduction in measured usage by 50% to 75%. Another common form of tampering involved simply bypassing the meter entirely or switching wires on the utility side of the meter to cause the rotor disk to rotate in the opposite direction – decrementing wattage counters to falsely indicate lower energy usage. In a similar tampering approach, the neutral wire would be removed to stop rotor movement and halt the counters entirely. Typically, energy thieves would remove evidence of tampering during the day to avoid detection by utility workers.

Figure 1: Traditional analog energy meters were susceptible to magnetic tampering and current tampering that often resulted in a 50% to75% reduction in measured usage. Smart meters remain inherently susceptible to the same problems but offer additional mechanisms to detect tampering.
Smart meters
The emergence of smart meters has both created additional opportunities for theft as well as enabled a broader set of sophisticated tamper-detection mechanisms. Specialized energy-metering system-on-chip (SoC) devices such as the Analog Devices ADE7763, Maxim Integrated 71M654xT, and STMicroelectronics STPM01/10 integrate energy measurement and metrology functionality with additional capabilities on a single chip. Using these devices, engineers can create sophisticated metering designs with few additional components (Figure 2). Without special precautions, however, these sophisticated smart-meter designs are no less inherently susceptible to tampering than their earlier mechanical counterparts.

Figure 2: Engineers can draw on highly integrated system-on-chip (SoC) devices to build smart meters with sophisticated metering capabilities and simplified connectivity with the smart grid through near-area networks (NAN) and with energy-management systems through home-area networks (HAN). (Courtesy of Maxim Integrated)
As with their earlier mechanical counterparts, however, smart meters still depend on external sensors for measuring energy usage. In particular, current-transformer (CT) sensors typically used in metering applications present a point of vulnerability to attacks using strong magnets. Placed near the current sensor, the external magnet introduces measurement errors by saturating the core of the CT device or otherwise distorting its output. Meter designers can mitigate this type of tampering by using magnetic shields or additional sensors to detect the presence of a strong external magnetic field. Alternatively, engineers can turn to less susceptible sensors based on shunt resistors or Rogowski coils such as the Pulse Electronics PA32XXNL series. Although the specific choice between these alternatives depends on metering requirements, both of these sensor types are immune to magnetic fields and so offer an attractive approach for mitigating this type of tampering.
Like conventional mechanical meters, however, smart meters remain vulnerable to tampering methods based on current manipulation. With this type of tampering, the energy thief would remove the neutral wire, swap live and neutral wires, or fault the load to reduce return current through the meter. In the past, mechanical meters could at best employ the relatively simple expedient of measuring rotor rotation and direction to detect current tampering. With SoC-based smart designs, however, engineers can employ more sophisticated methods that check for current balance between the live and neutral wires and flag any imbalance as an attempt at tampering.
For example, the STMicroelectronics STPM01/10 smart meter ICs provide built-in tamper-detection functionality. During normal operation, these devices measure the current in both live and neutral wire with a time domain multiplexing approach (Figure 3). During the time each channel is observed, the device calculates active-energy usage. If the device finds that the active-energy measurement for live and neutral wires is greater than a certain percentage of the averaged energy, it enters a tamper state.
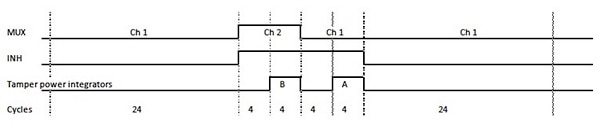
Figure 3: STMicroelectronics' STPM01 and STPM10 smart-meter ICs provide a dedicated tamper-detection mechanism that uses multiplexed measurements of live and neutral wires to find current tampering attempts. (Courtesy of STMicroelectronics)
In fact, this approach works if the measurements are both positive or negative for each channel. The device automatically enters its tamper state if the measurements for the two channels have a different sign; but even in this case, for its final energy calculations the device uses the channel that exhibits the higher absolute value. Engineers can select a difference threshold of 6.25% or 12.5%, offering a sufficiently wide margin to prevent false indications of tampering events. In addition, in single-wire mode, the device uses apparent energy rather than the active energy for tamper detection. Finally, to prevent tampering attempts designed to modify calibration parameters, the device stores calibration values in one-time programmable memory.
Advanced meters
For more advanced smart-meter designs, engineers typically combine separate analog front-end (AFE) ICs and MCUs to provide greater accuracy, higher performance, more functionality, or a combination of those attributes. While the AFE IC provides the measurement data, an MCU such as a device from Texas Instruments’ MSP430 family or Freescale Semiconductor’s Kinetis series handles energy calculations and applications execution. In fact, multicore MCUs such as the Atmel SAM4C series and NXP Semiconductors LPC43xx series are often used in these designs to separate revenue-related calculations from applications executions – partitioning metrology calculations in one core and non-revenue-related code in another.
Designers can augment these types of designs with tamper-detection functionality. For example, real-time clocks such as the STMicroelectronics M41ST87W can record tamper events. Able to retain their contents on battery power, these devices offer a relatively simple anti-tampering approach that remains relatively immune to accidental or purposeful power failure.
Along with protecting the data itself through the use of encryption techniques, secure energy-meter design needs to ensure that communications across the smart grid remain protected. Here, protection of the keys used for encryption is critical. Just as important, security protocols are required to ensure the communications connection is made with an authenticated host. For both key and authentication security, devices such as Atmel’s CryptoAuthentication EEPROMs and ATECC508A IC can interface with a host MCU to provide secure key storage and hardware-based authentication mechanisms.
Conclusion
Electricity theft relies on attacks on utility meters to present a falsified record of energy usage. With the movement to smart-meter designs, engineers need to adopt a range of methods to detect tampering attempts and resist modification of energy-usage data. For smart-meter designs, engineers can employ a variety of tamper detection and protection mechanisms using available energy-metering SoCs, MCUs, and other tamper-protection and security devices.
For more information about the parts discussed in this article, use the links provided to access product pages on the DigiKey website.
免责声明:各个作者和/或论坛参与者在本网站发表的观点、看法和意见不代表 DigiKey 的观点、看法和意见,也不代表 DigiKey 官方政策。










 中国
中国