Anti-Tamper Memory
2015-06-04
Tamper protection overview
Electronic systems often carry sensitive information such as passwords, personal data, encryption keys, or IPs. Attackers attempt to access these data by breaking into systems. Secure systems are designed to enable authorized access through password entry, and take action to protect valuable data or destroy sensitive data on detection of a tamper attempt. Examples of systems which need to protect data are security cameras or black box recorders where stored data should not be allowed to be modified; and ATMs or POS systems where personal data should not be allowed to be accessed. However, it is often a challenge to destroy data stored in low-power memory devices. Because low-power SRAMs are designed to have low leakage currents, they are capable of holding data even with zero voltage on power pin. Therefore, removal or shorting of power to ground is not enough to corrupt the stored data. It requires the application of negative voltage on the power pin to drain the charges in the memory cell.
An ideal anti-tamper memory must have a password entry feature and, in the event of tamper, it should be able to protect the data without allowing unauthorized access or self-destruct, depending on the application requirement. It must also be fast so that the destruct process is completed before interruption or further tampering.
nvSRAM – the solution
nvSRAM is a fast nonvolatile memory with an SRAM interface. The SRAM interface gives the nvSRAM a very high speed read and write access (down to 20 ns) and enables the nvSRAM to be infinitely written or read. If the power goes down, the data held in SRAM is transferred to the nonvolatile elements integrated with each SRAM cell using the charge stored in a small capacitor. On power up, the data is automatically transferred back to the SRAM. The parallel transfer of data from SRAM to the integrated nonvolatile elements means that the STORE (transfer of SRAM data to nonvolatile elements) takes time equivalent to only one EEPROM write operation. Store operation and recall (transfer of NV data to SRAM) operation can also be done through software commands.
Figure 1: nvSRAM - fast, easy, and secure.
In addition to the standard features mentioned above, nvSRAM offers the following anti-tamper protection features:
- Password protection to guard against accidental or malicious intrusion
- Upon tamper detection
- Protect data by preventing access to data, or
- Destroy data, destroy functionality, and/or physically damage
These features are unique in nvSRAM solutions and are faster than in most existing circuit solutions.
Tamper protection
Sensitive information such as cryptographic keys, sensitive algorithms, stored data, or intellectual property are stored in many applications such as Point of Sale (POS) terminals, Automatic Teller Machines (ATMs), credit card readers, networking (encryption), and energy metering. Attackers attempt to access these data by breaking into the systems. Therefore, these systems are designed to have tamper protection schemes. They are designed to detect tamper attempts and issue a signal to deactivate an ongoing transaction and prevent access or destroy any stored information before attackers can access sensitive information. While tamper detection can be done immediately, it is a difficult task to delete stored data.
Cypress’s anti-tamper memory products address these concerns and provide the following tamper protect features:
- Password protected access
- Data protection or data destruction on tamper
Password protected access in nvSRAM
It is possible to configure the nvSRAM to provide password protected access. In this configuration, instead of performing the normal power-up recall sequence on power up, the part waits for the user to enter a 5 byte password followed by an End Password Entry soft sequence. The End Password Entry soft sequence is a specific seven address read sequence. If you enter the correct password, the part completes the boot up sequence and is ready for the normal nvSRAM operations. If you enter the incorrect password three times or you do not enter the right password within a specified period of time, the part locks up or fills the SRAM memory with random data, as the application requirement may be. The part can be configured to additionally destroy the functionality and cause physical damage to the chip.
Changing the password
The anti-tamper memory is shipped with a default 5 byte password. You can change the password through software control. To change the password, you must run a seven address sequence which initiates the password change process. Then, enter the current password followed by the new password twice.
Password entry at power up
On each power up, instead of performing the normal power-up recall sequence, the part waits for the user to enter the password. After receiving the correct password, the part completes the boot up sequence and is ready for the normal nvSRAM operations. If you enter the incorrect password three times or you do not enter the right password within a specified duration of time, the part executes lock up or destruct sequence.
The anti-tamper memory can be configured to protect the data by locking up the part on password failure. The part can be enabled by password on power cycling.
The anti-tamper memory can be configured to destroy data in one of the following three methods:
- Destroy the data in the memory
- Destroy the data and destroy the memory functionality
- Destroy the data and functionality, and also cause physical damage to the part
These three methods are explained in the following sections.
Data Destruction upon Tamper Detection
Failure to enter the valid password within the required time indicates tamper and anti-tamper systems to require that the existing data in the memory is destroyed.
Destroy data in the memory
This feature is for the lowest security requirement. The part is configured to destroy the data immediately on failure to enter the correct password. This is done by erasing all the SONOS cells and recalling the bogus memory in the SRAM and is executed in 5 ms.
Device data and destroy device functionality
As a higher level of protection for the security application, the part can be configured to destroy the stored data on failure to enter the password and, in addition, render the memory unusable. The data is destroyed and all the nonvolatile cells are erased, and the SRAM is filled with the bad data. Subsequently, the part performs a power on reset (POR) to render the part unbootable. The time taken to complete both data destruction and functional destruction is only 8 ms.
Device data, destroy device functionality, and cause physical damage to the chip
It is also possible to damage the chip after the memory is destroyed and the device does not function. In this configuration, the device applies the runaway condition to the circuits which perform the Store. This process takes 60 seconds.
A typical power-up sequence in anti-tamper memory is illustrated in Figure 2.
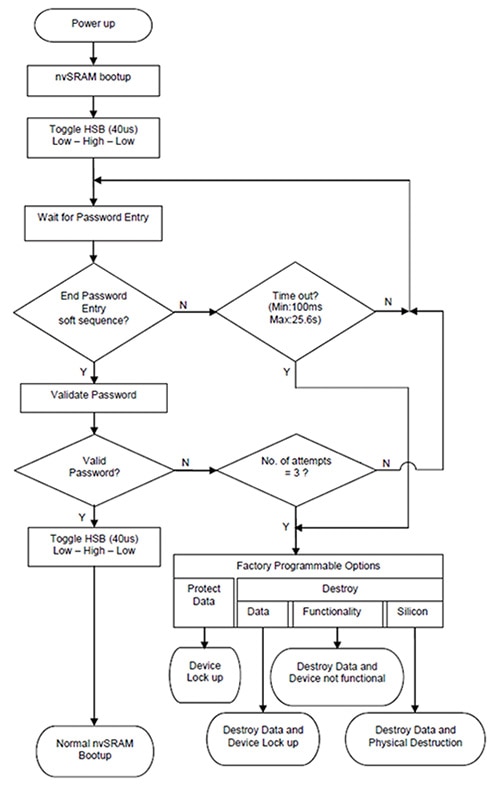
Figure 2: Power-up sequence in anti-tamper memory.
Data destruction using software commands
In addition to the password features, Cypress’s nvSRAM can be configured to destroy SRAM data based on controller commands. Most secure applications have a built-in tamper detect feature that triggers RAM erase signals for both internal and external RAMs in case of an attempted tamper. The external RAMs are then erased by applying negative voltage to the VCC pin of the RAM that discharges the memory cell charges. This process needs external components such as a negative voltage charge pump with its associated components, and is also slow (on the order of 1/100 of a millisecond to 1 second).
In the case of anti-tamper memory, this process can be completed without any additional components and in a much shorter 5 ms. When tamper is detected, the controller must send out a specific seven address read sequence to the anti-tamper memory. At read speeds of 45 ns, this takes about 300 ns. At the seventh read, the memory initiates the data destruction sequence. Depending on user requirement, the controller can be programmed to send out the specific sequence to execute any one of the following data destructions:
- Destroy the data in the memory
- Destroy the data and destroy the memory functionality
- Destroy the data and functionality and also cause physical damage to the part
These three data destruction options are explained in the section Data Destruction upon Tamper Detection above. As described earlier, the data destruction is done in 5 ms which is about 200 times faster than the conventional SRAM discharge method.
Summary
In addition to being the fastest nonvolatile SRAM solution, Cypress’s anti-tamper memory provides unique tamper protect features. The device’s anti-tamper response can be configured to suit specific application requirements. It has the password access feature and the capability to protect data or to destroy data, functionality, and can cause physical destruction on failure to enter the correct password. Additionally, it can cause destruction through controller initiated commands. These features make the anti-tamper memory an ideal device in secure applications.
The Cypress Anti-Tamper Memory can be customized to meet your application needs by utilizing any of the tamper protection options individually or concurrently.
免责声明:各个作者和/或论坛参与者在本网站发表的观点、看法和意见不代表 DigiKey 的观点、看法和意见,也不代表 DigiKey 官方政策。







 中国
中国