Next-Generation Sensor Solutions for Security and Verification Systems
投稿人:电子产品
2016-04-01
Security concerns are among the oldest motivators driving development of new sensor technology. From the old trip wires of yesteryear to modern-day olfactory pheromone detectors, the need to know when someone is present, or what someone is carrying with them, is essential to counteracting a potential threat.
This article looks at technologies and components that can be used in next-generation security sensors and screening systems. It will explore real-time sensor systems developed to extract and verify identity as well as determine if individuals or the substances they carry with them are potentially dangerous. As an example we will consider design solutions intended for a next-generation TSA screening station. All parts, data sheets, tutorials, reference designs, and development kits referenced here can be found online on DigiKey’s website.
A big responsibilityMaking good security decisions involves the successful combination of information technology and real-time sensor data. Since physical papers can be forged and identification cards stolen, there is an increasing burden on sensor technology to provide a tamper-proof means of accurate, real-time verification that someone is who they claim to be. What’s more, the presence of modern threats like biological, radiation, and chemical weapons means sensor technology is also saddled with the responsibility of ascertaining and thwarting these threats with a minimum of false positives.
Being able to quickly weigh things such as backpacks can give security providers a first indication that something might be out of order. Engineers tasked with developing sensor-based designs for this application can use a variety of readily available components such as the Microchip MCP3421DM-WS, an eval and test board that implements a complete free reference design. This includes schematic, Gerbers, BOM, and code. The eval board and design implement a fully functional weight scale for up to 2 Kg with 1 mV/V sensitivity. It uses a low-cost load cell but leaves provision to accept external load-cell sensors. This design houses an embedded microcontroller and uses a USB to communicate back to a host development and test unit.
Another example without an embedded processor comes from Analog Devices with its EVAL-CN0216-SDPZ precision weight scale evaluation and demo board. The reference design for this part also includes schematics, layouts, and BOMs, and is part of the company’s “Circuits from the Lab” series. The design uses the company’s AD7791 24-bit Sigma-Delta ADC with external ADA4528-1 zero-drift amplifiers.
Height can be a potentially important parameter in identity verification. Like a mug-shot height scale, a visible or invisible scale can be located at an examination point such as the TSA checkpoint at airports. We’ve all experienced modern flying spot X-Ray scanners, which will typically make you place your hands in pre-defined locations while the scans take place. This can also provide a calibrated point where a height reading can take place. An IR illuminator can allow a video camera to take a snapshot and pick up the height scale covertly. A CCD camera will pick up IR radiation and make it visible in video streams. An alternative solution is to have the scale etched into the reticule of the lens.
Video scanning can capture more than just height. A close-up image will allow facial-recognition software to independently check its database. Unlike older manual photo-matching systems, current facial-recognition systems have proven themselves as valid law enforcement tools, and are even available to private citizens such as that implemented on enhanced reality data systems like Google Glass.
Video-parameter extraction depends on capturing a quality image, and then performing edge and boundary enhancements, which bring out key points that can be examined mathematically (Figure 1). Ratios between the center of eyes and ears, facial muscle spans, cheekbones, and other rather easily discernable features can be extracted and basically used as lookup table parameters to find matches.

Figure 1: Video sensors can extract a lot of personal information, including the ability to perform facial recognition to verify an identity. Access to databases allows real-time sensor data to trigger an alert to security agents right away.
It should be noted that video also captures eye color and hair color; with controlled lighting in the examination area these are reliable readings. Examination of video data requires a fair amount of processing and resources, but can easily be tested and developed using standard, off-the-shelf technology.
New video support devices are being introduced thanks to the ever-increasing capabilities and demands of smartphone cameras. Video capture and development kits like the Analog Devices EVAL-ADV7842-7511P provide video decoding and processing with an on-board DSP. With video digitizer support of up to 170 MHz, this demo and development kit supports 3D video formats up to 1080p with 30- and 26-bit color depth. RGB graphics can be digitized up to UXGA resolution (1600 x 1280) and dual-adaptive HDMI equalized interfaces allow parallel transport of image data for archiving and downstream processing. High-enough resolution image sensors can also be used to perform retinal scans, which are more reliable than fingerprints in many people’s eyes (pun intended).
When screening takes place, asking subjects a simple question will present real-time sensors with a voice sample. Speaker identification using voice-print parameters is another usable identification technique. As long as DSP functionality is being employed in the video stream processing, devoting some processing resources to voice printing is essentially a freebie.
Use of thermal imaging at airport screening stations has been in effect for some time. During the Ebola virus scare, airports used thermal cameras and technologies to discern if travelers were sick, had fever, or displayed other unusual thermal characteristics. Thermal technology has even been used to detect if someone is lying since real-time temperature changes reflect the heightened metabolic functions associated with nervousness. In addition, thermal imaging may detect on-body explosives, another technique that has already been successfully used.
While thermal cameras such as the Lepton series from FLIR are generally priced higher than standard CMOS image sensor cameras, thanks to newer thermal-detector material advances these once quite expensive sensor arrays are now much more cost effective.
A good example of a readily available forward-looking infrared thermal camera sensor is the FLIR Lepton model 500-0643-00, an 80 x 60 element thermal imager capable of imaging in half a second. The 150 mw low-power sensor is smaller than a dime so it can easily be incorporated into the examination area near an LCD display.
Chemical, biological, and radiological sensorsChemical and bacteria-sensing systems are still very specialized disciplines. The most widely used technology employs ultraviolet light sources. Many chemical agents used in explosives fluoresce at ultraviolet wavelengths and both solid-state UV emitters and CCFL-based UV emitters such as the BF23312-24B from JKL Components can be used to examine fingers and luggage to look for evidence of recent exposure to these chemical agents (Figure 2). There are even UV-sensor development kits available.

Figure 2: UV light can cause many of the constituent elements used in explosives to fluoresce. UV imaging can detect if someone has been in contact with these agents.
Items such as the ML8511_REFBOARD from ROHM Semiconductor can be used to help drive this solution.
Research using MEMs, nanotechnology, and microfluidics is showing promise of creating fast, low-cost, and accurate sensing systems capable of detecting a variety of catalogued and classified pathogens and particles.
Some of this technology is emerging now, like the AS-MLV-P2 gas sensor from ams. The voltage-output sensor is intended for air quality use and is designed to detect a broad range of volatile organic compounds. Two heater electrodes excite the platinum sense elements that react to several gases in consistent and reliable ways (Figure 3).
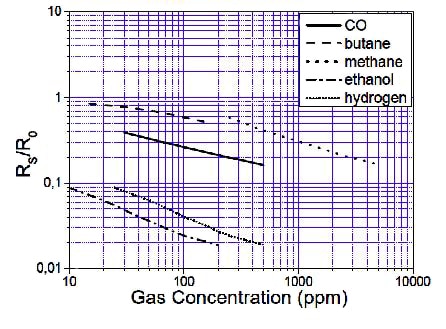
Figure 3: Newer nanotechnologies are yielding specific gas sensors that can detect possible out-gasing from the presence of restricted or explosive chemicals.
Similarly, methane, alcohol/benzene, and carbon monoxide sensors are also available for use. Expect to see more as MEMs and microfluidics merge with semiconductor systems to provide so-called laboratories-on-a-chip even capable of performing real-time genetic sequencing for specific markers.
Geiger-counter technology is still the predominant technology for radiation detection, although low-cost detectors can even be made from a neon bulb1. It works like this: voltage levels are raised to just below an ionizing threshold. As particle radiation travels through the neon, it causes ionization and creates a momentary pulse. This can be amplified to a speaker to hear those familiar ticks, or, fed into a DSP to accumulate a gated count value.
RF transpondingEven though cellphones, tablets, laptops, and other RF emitters are separated from you as you pass through a security checkpoint, vital information also can be gathered from the garments you wear. Modern RFID second-generation transponder tags potentially can allow a reader to query your garments, purses, sneakers, belts, and anything else that can embed these sub-25-cent tags. The UHF-based Gen II protocol could allow readers like the ThingMagic M6E-NANO embedded UHF RFID module to extract information from your clothing. For example, if a TSA agent feels someone is suspicious, even though there may be nothing obvious to be concerned about, he or she could in a future scenario write an alert note in an attached RFID tag for the next security agent to read.
In summary, security concerns are more heightened today than ever before. As a result, technological verification of identity as well as real-time threat assessments is likely to be in great demand. As this article has shown, the underlying technologies are here today and are expected to be in wider use tomorrow.
For more information use the links provided to access product pages on the DigiKey website.
References
免责声明:各个作者和/或论坛参与者在本网站发表的观点、看法和意见不代表 DigiKey 的观点、看法和意见,也不代表 DigiKey 官方政策。




